The Gameshark Advance was the original cheat device for the Gameboy Advance. While more functional than the cheat devices for the Gameboy, it is still far less functional than its equivalent for the N64. The GSA's code types include 8-, 16-, and 32-bit writes, a slide code, a 16-bit If Equal To conditional, and a 16-bit ROM patch. The GSA also does not provide a code searching feature, something that had been provided in all incarnations for the Gameboy. Finally, the codes are encrypted, a first for any handheld cheat device. In Europe, the Gameshark is referred to as the Action Replay. The two products shared a name starting with revision 3, an entirely different product referred to as ARv3.
After Interact went bankrupt and sold the Gameshark name rights, Datel decided to directly sell their product in North America. Because of this, the Action Replay name became used in both North America and Europe. This name synchrony began with the third revision of the AR, for the GBA. The ARv3 adds a massive number of code types, 114 in total. Additionally, the ARv3 uses a different encryption, although this has been cracked as well.
| Type |
Description |
| Normal RAM Write Codes |
| 00a0aaaa xxxxxxyy |
8-bit RAM Write/Fill
Fills the area from 0a00aaaa to 0a00aaaa + xxxxxx with yy. |
| 02a0aaaa xxxxyyyy |
16-bit RAM Write/Fill
Fills the area from 0a00aaaa to 0a00aaaa + xxxx * 2 with yyyy. |
| 04a0aaaa yyyyyyyy |
32-bit RAM Write
Writes yyyyyyyy to 0a00aaaa. |
| Pointer RAM Write Codes |
| 40a0aaaa xxxxxxyy |
8-bit Pointer RAM Write
Writes yy to the address located in 0a00aaaa + xxxxxx. |
| 42a0aaaa xxxxyyyy |
16-bit Pointer RAM Write
Writes yyyy to the address located in 0a00aaaa + xxxx * 2. |
| 44a0aaaa yyyyyyyy |
32-bit Pointer RAM Write
Writes yyyyyyyy to the address located in 0a00aaaa. |
| Add Codes |
| 80a0aaaa 000000yy |
8-bit Add Code
Adds yy to the byte stored at 0a00aaaa. |
| 82a0aaaa 0000yyyy |
16-bit Add Code
Adds yyyy to the halfword stored at 0a00aaaa. |
| 84a0aaaa yyyyyyyy |
32-bit Add Code
Adds yyyyyyyy to the word stored at 0a00aaaa. |
| Write to IO Registers |
| C600aaaa 0000yyyy |
16-bit IO Register Write
Writes yyyy to 0x0400aaaa. |
| C700aaaa yyyyyyyy |
32-bit IO Register Write
Writes yyyyyyyy to 0x0400aaaa. |
| If Equal To |
| 08a0aaaa 000000yy |
8-bit If Equal To (1 line)
Executes next code only if yy is equal to the byte stored at 0a00aaaa. |
| 48a0aaaa 000000yy |
8-bit If Equal To (2 lines)
Executes next two codes only if yy is equal to the byte stored at 0a00aaaa. |
| 88a0aaaa 000000yy |
8-bit If Equal To (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is equal to the byte stored at 0a00aaaa. |
| C8a0aaaa 000000yy |
8-bit If Equal To (Disable Codes)
All codes are disabled when the byte at 0a00aaaa is not equal to yy. |
| 0Aa0aaaa 0000yyyy |
16-bit If Equal To (1 line)
Executes next code only if yy is equal to the halfword stored at 0a00aaaa. |
| 4Aa0aaaa 0000yyyy |
16-bit If Equal To (2 lines)
Executes next two codes only if yy is equal to the halfword stored at 0a00aaaa. |
| 8Aa0aaaa 00000yyyy |
16-bit If Equal To (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is equal to the halfword stored at 0a00aaaa. |
| CAa0aaaa 0000yyyy |
16-bit If Equal To (Disable Codes)
All codes are disabled when the halfword at 0a00aaaa is not equal to yy. |
| 0Ca0aaaa yyyyyyyy |
32-bit If Equal To (1 line)
Executes next code only if yy is equal to the word stored at 0a00aaaa. |
| 4Ca0aaaa yyyyyyyy |
32-bit If Equal To (2 lines)
Executes next two codes only if yy is equal to the word stored at 0a00aaaa. |
| 8Ca0aaaa yyyyyyyy |
32-bit If Equal To (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is equal to the word stored at 0a00aaaa. |
| CCa0aaaa yyyyyyyy |
32-bit If Equal To (Disable Codes)
All codes are disabled when the word at 0a00aaaa is not equal to yy. |
| If Not Equal To |
| 10a0aaaa 000000yy |
8-bit If not equal To (1 line)
Executes next code only if yy is not equal to the byte stored at 0a00aaaa. |
| 50a0aaaa 000000yy |
8-bit If not equal To (2 lines)
Executes next two codes only if yy is not equal to the byte stored at 0a00aaaa. |
| 90a0aaaa 000000yy |
8-bit If not equal To (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is not equal to the byte stored at 0a00aaaa. |
| D0a0aaaa 000000yy |
8-bit If not equal To (Disable Codes)
All codes are disabled when the byte at 0a00aaaa is not not equal to yy. |
| 12a0aaaa 0000yyyy |
16-bit If not equal To (1 line)
Executes next code only if yy is not equal to the halfword stored at 0a00aaaa. |
| 52a0aaaa 0000yyyy |
16-bit If not equal To (2 lines)
Executes next two codes only if yy is not equal to the halfword stored at 0a00aaaa. |
| 92a0aaaa 00000yyyy |
16-bit If not equal To (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is not equal to the halfword stored at 0a00aaaa. |
| D2a0aaaa 0000yyyy |
16-bit If not equal To (Disable Codes)
All codes are disabled when the halfword at 0a00aaaa is not not equal to yy. |
| 14a0aaaa yyyyyyyy |
32-bit If not equal To (1 line)
Executes next code only if yy is not equal to the word stored at 0a00aaaa. |
| 54a0aaaa yyyyyyyy |
32-bit If not equal To (2 lines)
Executes next two codes only if yy is not equal to the word stored at 0a00aaaa. |
| 94a0aaaa yyyyyyyy |
32-bit If not equal To (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is not equal to the word stored at 0a00aaaa. |
| D4a0aaaa yyyyyyyy |
32-bit If not equal To (Disable Codes)
All codes are disabled when the word at 0a00aaaa is not not equal to yy. |
| If less than (signed) |
| 18a0aaaa 000000yy |
8-bit If less than (signed) (1 line)
Executes next code only if yy is less than (signed) the byte stored at 0a00aaaa. |
| 58a0aaaa 000000yy |
8-bit If less than (signed) (2 lines)
Executes next two codes only if yy is less than (signed) the byte stored at 0a00aaaa. |
| 98a0aaaa 000000yy |
8-bit If less than (signed) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is less than (signed) the byte stored at 0a00aaaa. |
| D8a0aaaa 000000yy |
8-bit If less than (signed) (Disable Codes)
All codes are disabled when the byte at 0a00aaaa is not less than (signed) yy. |
| 1Aa0aaaa 0000yyyy |
16-bit If less than (signed) (1 line)
Executes next code only if yy is less than (signed) the halfword stored at 0a00aaaa. |
| 5Aa0aaaa 0000yyyy |
16-bit If less than (signed) (2 lines)
Executes next two codes only if yy is less than (signed) the halfword stored at 0a00aaaa. |
| 9Aa0aaaa 00000yyyy |
16-bit If less than (signed) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is less than (signed) the halfword stored at 0a00aaaa. |
| DAa0aaaa 0000yyyy |
16-bit If less than (signed) (Disable Codes)
All codes are disabled when the halfword at 0a00aaaa is not less than (signed) yy. |
| 1Ca0aaaa yyyyyyyy |
32-bit If less than (signed) (1 line)
Executes next code only if yy is less than (signed) the word stored at 0a00aaaa. |
| 5Ca0aaaa yyyyyyyy |
32-bit If less than (signed) (2 lines)
Executes next two codes only if yy is less than (signed) the word stored at 0a00aaaa. |
| 9Ca0aaaa yyyyyyyy |
32-bit If less than (signed) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is less than (signed) the word stored at 0a00aaaa. |
| DCa0aaaa yyyyyyyy |
32-bit If less than (signed) (Disable Codes)
All codes are disabled when the word at 0a00aaaa is not less than (signed) yy. |
| If greater than (signed) |
| 20a0aaaa 000000yy |
8-bit If greater than (signed) (1 line)
Executes next code only if yy is greater than (signed) the byte stored at 0a00aaaa. |
| 60a0aaaa 000000yy |
8-bit If greater than (signed) (2 lines)
Executes next two codes only if yy is greater than (signed) the byte stored at 0a00aaaa. |
| A0a0aaaa 000000yy |
8-bit If greater than (signed) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is greater than (signed) the byte stored at 0a00aaaa. |
| E0a0aaaa 000000yy |
8-bit If greater than (signed) (Disable Codes)
All codes are disabled when the byte at 0a00aaaa is not greater than (signed) yy. |
| 21a0aaaa 0000yyyy |
16-bit If greater than (signed) (1 line)
Executes next code only if yy is greater than (signed) the halfword stored at 0a00aaaa. |
| 61a0aaaa 0000yyyy |
16-bit If greater than (signed) (2 lines)
Executes next two codes only if yy is greater than (signed) the halfword stored at 0a00aaaa. |
| A1a0aaaa 00000yyyy |
16-bit If greater than (signed) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is greater than (signed) the halfword stored at 0a00aaaa. |
| E1a0aaaa 0000yyyy |
16-bit If greater than (signed) (Disable Codes)
All codes are disabled when the halfword at 0a00aaaa is not greater than (signed) yy. |
| 22a0aaaa yyyyyyyy |
32-bit If greater than (signed) (1 line)
Executes next code only if yy is greater than (signed) the word stored at 0a00aaaa. |
| 62a0aaaa yyyyyyyy |
32-bit If greater than (signed) (2 lines)
Executes next two codes only if yy is greater than (signed) the word stored at 0a00aaaa. |
| A2a0aaaa yyyyyyyy |
32-bit If greater than (signed) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is greater than (signed) the word stored at 0a00aaaa. |
| E2a0aaaa yyyyyyyy |
32-bit If greater than (signed) (Disable Codes)
All codes are disabled when the word at 0a00aaaa is not greater than (signed) yy. |
| If less than (unsigned) |
| 28a0aaaa 000000yy |
8-bit If less than (unsigned) (1 line)
Executes next code only if yy is less than (unsigned) the byte stored at 0a00aaaa. |
| 68a0aaaa 000000yy |
8-bit If less than (unsigned) (2 lines)
Executes next two codes only if yy is less than (unsigned) the byte stored at 0a00aaaa. |
| A8a0aaaa 000000yy |
8-bit If less than (unsigned) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is less than (unsigned) the byte stored at 0a00aaaa. |
| E8a0aaaa 000000yy |
8-bit If less than (unsigned) (Disable Codes)
All codes are disabled when the byte at 0a00aaaa is not less than (unsigned) yy. |
| 2Aa0aaaa 0000yyyy |
16-bit If less than (unsigned) (1 line)
Executes next code only if yy is less than (unsigned) the halfword stored at 0a00aaaa. |
| 6Aa0aaaa 0000yyyy |
16-bit If less than (unsigned) (2 lines)
Executes next two codes only if yy is less than (unsigned) the halfword stored at 0a00aaaa. |
| AAa0aaaa 00000yyyy |
16-bit If less than (unsigned) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is less than (unsigned) the halfword stored at 0a00aaaa. |
| EAa0aaaa 0000yyyy |
16-bit If less than (unsigned) (Disable Codes)
All codes are disabled when the halfword at 0a00aaaa is not less than (unsigned) yy. |
| 2Ca0aaaa yyyyyyyy |
32-bit If less than (unsigned) (1 line)
Executes next code only if yy is less than (unsigned) the word stored at 0a00aaaa. |
| 6Ca0aaaa yyyyyyyy |
32-bit If less than (unsigned) (2 lines)
Executes next two codes only if yy is less than (unsigned) the word stored at 0a00aaaa. |
| ACa0aaaa yyyyyyyy |
32-bit If less than (unsigned) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is less than (unsigned) the word stored at 0a00aaaa. |
| ECa0aaaa yyyyyyyy |
32-bit If less than (unsigned) (Disable Codes)
All codes are disabled when the word at 0a00aaaa is not less than (unsigned) yy. |
| If greater than (unsigned) |
| 30a0aaaa 000000yy |
8-bit If greater than (unsigned) (1 line)
Executes next code only if yy is greater than (unsigned) the byte stored at 0a00aaaa. |
| 70a0aaaa 000000yy |
8-bit If greater than (unsigned) (2 lines)
Executes next two codes only if yy is greater than (unsigned) the byte stored at 0a00aaaa. |
| B0a0aaaa 000000yy |
8-bit If greater than (unsigned) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is greater than (unsigned) the byte stored at 0a00aaaa. |
| F0a0aaaa 000000yy |
8-bit If greater than (unsigned) (Disable Codes)
All codes are disabled when the byte at 0a00aaaa is not greater than (unsigned) yy. |
| 32a0aaaa 0000yyyy |
16-bit If greater than (unsigned) (1 line)
Executes next code only if yy is greater than (unsigned) the halfword stored at 0a00aaaa. |
| 72a0aaaa 0000yyyy |
16-bit If greater than (unsigned) (2 lines)
Executes next two codes only if yy is greater than (unsigned) the halfword stored at 0a00aaaa. |
| B2a0aaaa 00000yyyy |
16-bit If greater than (unsigned) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is greater than (unsigned) the halfword stored at 0a00aaaa. |
| F2a0aaaa 0000yyyy |
16-bit If greater than (unsigned) (Disable Codes)
All codes are disabled when the halfword at 0a00aaaa is not greater than (unsigned) yy. |
| 34a0aaaa yyyyyyyy |
32-bit If greater than (unsigned) (1 line)
Executes next code only if yy is greater than (unsigned) the word stored at 0a00aaaa. |
| 74a0aaaa yyyyyyyy |
32-bit If greater than (unsigned) (2 lines)
Executes next two codes only if yy is greater than (unsigned) the word stored at 0a00aaaa. |
| B4a0aaaa yyyyyyyy |
32-bit If greater than (unsigned) (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy is greater than (unsigned) the word stored at 0a00aaaa. |
| F4a0aaaa yyyyyyyy |
32-bit If greater than (unsigned) (Disable Codes)
All codes are disabled when the word at 0a00aaaa is not greater than (unsigned) yy. |
| If AND |
| 38a0aaaa 000000yy |
8-bit If AND (1 line)
Executes next code only if yy AND the byte stored at 0a00aaaa is not equal to 0. |
| 78a0aaaa 000000yy |
8-bit If AND (2 lines)
Executes next two codes only if yy AND the byte stored at 0a00aaaa is not equal to 0. |
| B8a0aaaa 000000yy |
8-bit If AND (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy AND the byte stored at 0a00aaaa is not equal to 0. |
| F8a0aaaa 000000yy |
8-bit If AND (Disable Codes)
All codes are disabled when the byte at 0a00aaaa AND yy is 00. |
| 39a0aaaa 0000yyyy |
16-bit If AND (1 line)
Executes next code only if yy AND the halfword stored at 0a00aaaa is not equal to 0. |
| 79a0aaaa 0000yyyy |
16-bit If AND (2 lines)
Executes next two codes only if yy AND the halfword stored at 0a00aaaa is not equal to 0. |
| B9a0aaaa 00000yyyy |
16-bit If AND (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy AND the halfword stored at 0a00aaaa is not equal to 0. |
| F9a0aaaa 0000yyyy |
16-bit If AND (Disable Codes)
All codes are disabled when the halfword at 0a00aaaa AND yy is 00. |
| 3Aa0aaaa yyyyyyyy |
32-bit If AND (1 line)
Executes next code only if yy AND the word stored at 0a00aaaa is not equal to 0. |
| 7Aa0aaaa yyyyyyyy |
32-bit If AND (2 lines)
Executes next two codes only if yy AND the word stored at 0a00aaaa is not equal to 0. |
| BAa0aaaa yyyyyyyy |
32-bit If AND (Multi-line)
All subsequent codes until the z20 code type or end of code list are executed only if yy AND the word stored at 0a00aaaa is not equal to 0. |
| FAa0aaaa yyyyyyyy |
32-bit If AND (Disable Codes)
All codes are disabled when the word at 0a00aaaa AND yy is 00. |
| Always... codes |
| 0Ea0aaaa xxxxxxxx |
Always skip next line |
| 4Ea0aaaa xxxxxxxx |
Always skip next two lines |
| 8Ea0aaaa xxxxxxxx |
Always skip remaining codes |
| CEa0aaaa xxxxxxxx |
Always skip all codes |
| One line special codes |
| 00000000 xxxxxxxx |
End of code list
No codes after this point are executed. |
| 00000000 0800xx00 |
Slowdown code
The AR performs xx loops per code cycle, slowing the game down. |
| Two line special codes |
00000000 10a0aaaa
000000xx 00000000 |
8-bit AR Button RAM Write
Writes xx to 0a00aaaa when the AR Button is pressed. |
00000000 12a0aaaa
0000xxxx 00000000 |
16-bit AR Button RAM Write
Writes xxxx to 0a00aaaa when the AR Button is pressed. |
00000000 14a0aaaa
xxxxxxxx 00000000 |
32-bit AR Button RAM Write
Writes xxxxxxxx to 0a00aaaa when the AR Button is pressed. |
00000000 18a0aaaa
0000xxxx 00000000 |
16-bit ROM Patch
Patches 0x08000000 + (0a00aaaa >> 2) with xxxx. |
00000000 1Aa0aaaa
0000xxxx 00000000 |
16-bit ROM Patch
Patches 0x08000000 + (0a00aaaa >> 2) with xxxx. |
00000000 1Ca0aaaa
0000xxxx 00000000 |
16-bit ROM Patch
Patches 0x08000000 + (0a00aaaa >> 2) with xxxx. |
00000000 1Ea0aaaa
0000xxxx 00000000 |
16-bit ROM Patch
Patches 0x08000000 + (0a00aaaa >> 2) with xxxx. |
| 00000000 40000000 |
Execute codes normally
All conditionals currently going on do not apply after this point. |
| 00000000 60000000 |
Execute all following codes
All following codes are executed regardless of anything else. |
00000000 80a0aaaa
000000xx vvddiiii |
8-bit slide code
Writes dd bytes, starting at the address 0a00aaaa with the value xx and incrementing the address by iiii and the value by vv each iteration. |
00000000 82a0aaaa
0000xxxx vvddiiii |
16-bit slide code
Writes dd halfwords, starting at the address 0a00aaaa with the value xxxx and incrementing the address by iiii * 2 and the value by vv each iteration. |
00000000 84a0aaaa
xxxxxx vvddiiii
80000000 00000000 |
32-bit slide code
Writes dd words, starting at the address 0a00aaaa with the value xxxxxxxx and incrementing the address by iiii * 4 and the value by vv each iteration. The final line is needed to prevent a bug in the AR from occurring. |
| Special Codes |
| C4aaaaaa 00000bcd |
Master Code
Hooks the address 08aaaaaa for the code handler. if b is 1, the AR switch must be turned off when the game starts. Otherwise, it doesn't matter. c determines the number of codes the AR processes at a time. d is the type of hook. 0 is BL and 1 is Push LR then BL. |
| xxxxxxxx 001DC0DE |
ID Code
Used by the AR to auto-detect games. xxxxxxxx should be the word at 0x080000AC. |
| DEADFACE xxxxxxxx |
DEADFACE
Changes the encryption seeds. |
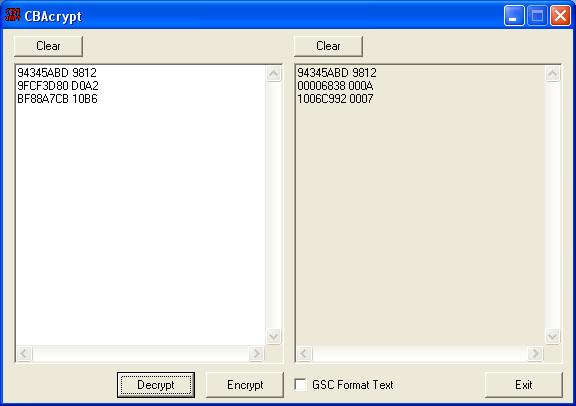
To create a master code for the Gameshark or Action Replay, a ROM of the game will be required, as well as AR Crypt. In AR Crypt, go to Special, then "Find Master Code and ID Code"; Load the ROM, and the master codes will be listed. Test each master code individually with a normal code. If the code works, then the master code being used is a legitimate master code. If AR Crypt does not come up with any results or non of the possible master codes works, a non-standard master code must be hacked.
The information in this section is based on a post originally by Parasyte.
Load Baulder's Gate up into VBA-SDL and enter the gameplay part of the game. Then load up a hex editor, open the rom, and search for 0x0047C0460847C046. This is the beginning of the long branch routine. For Baulder's Gate, it's at 0x006A9888 which is GBA address 0x086A9888. It disassembles to:
etc. These bx instructions are what we want to try to hook. What we are looking for is a bx instruction which is executed many times per second. Start with the bx r0. Tell VBA-SDL to break whenever that instruction is executed (bt 086A9888) and have the game resume (c). The game doesn't break, so this isn't what we want. Go back to the debugger (F11) and move on to bx r1. Set a breakpoint on that and resume gameplay. The game breaks. This is good. Copy down the value of R1 (since we are testing bx r1) and resume gameplay. It will break again. Copy down the new value of R1. Continue this process until it appears that all the possible values r1 have been copied. For this game, the values are 0x03003ef8, 0x0869FC05, 0x0869E145, 0x02000634, 0x02000514, 0x0869E3D5, and 0x0869E0D9. Now delete the breakpoint and move to another area (say, the tavern), and repeat the process. Here, the values obtained are 0x0869E3D5, 0x0869D5A1, 0x0869D165, 0x0869C881, 0x03003EF8, 0x0869FC05, 0x0869D81D, and 0x0869CF61. Now, find the common addresses. They are 0x03003EF8, 0x0869FC05, and 0x0869E3D5. Now it's time to make the mastercode.
One by one, search for each of the values in the ROM. Starting with 0x03003EF8, we must first rearrange this into the order it will appear in the ROM. Divide it into seperate bytes (0x03, 0x00, 0x3E, and 0xF8), then reverse the order, giving us 0xF83E0003. Search for this in the ROM. It is not present. Move to the next value, 0x0869FC05. Searching for 0x05FC6908 turns up four locations. This is not good. Any one of the four could be correct or, even worse, they could each be correct in a seperate part of the game. Go to the final value, 0x0869E3D5. Searching for 0xD5E36908 turns up only one location! Success. The location is 0x007EF48C. Turn the 00 into C4, and add 000084x1 as the value, where x is the register value used (r1 here). The final code is C47EF48C 00008411. If the code is being made for the Gameshark, the address should have the initial two zeros replaced with 48, and the value should be 000001x1, with x still being the register. For Gameshark, the final decrypted could is F87EF48C 00000111.
It is impossible to hack a universal master code for Phantasy Star Collection, because it contains four executables. The intro does not need a master code, but each of the other three executables (the three games) require a seperate master code. For Phantasy Star II and Phantasy Star III, creating a master code is simple enough. However, for Phantasy Star, there is a problem. The Phantasy Star exectuable is located at 0x08738000, and it is impossible to create a standard BL-type master code from any address above 0x0840001C. This is further complicated by the fact that the long branch routine does not exist in the Phantasy Star executable, so creating a master code the same way as for Baulder's Gate will not work. In this case, we shall take a different approach - find the interrupt handler. These are executed several times per second, so they are perfect.
Load up Phantasy Star Collection in VBA-SDL-H. The GBA interrupt vector is always located at 0x03007FFC. Use the mw command to display the word there; it should be a pointer. For me, it is 0x020207d0. This is an ARM address, because it is an even number. Had it been THUMB, it would have been 0x020207d1. Disassemble the arm (da) starting at 0x020207d0. Here is what I have:
This code loads pointer 0x02000070 into r1. Then, it adds r2 to it.Finally, it loads a pointer from that address into r0 and branches to that address. This is a prime example of a jump table (large amount of pointers stored in RAM). Dump the jump table from 0x02000070 with the mw command:
02000070 087384A1 0873A9FD 0873AA01 0873A9FD
02000080 0873A9FD 0873AA21 0876CA91 0873A9FD
02000090 0873A9FD 0873A9FD 0873A9FD 0873A9FD
020000A0 0873A9FD 0873A9FD 00000000 00000000
All of these pointers are odd numbers, which means they are all pointers to THUMB instructions. There are five in total: 0x087384A1, 0x0873A9FD, 0x0873AA01, 0x0873AA21, and 0x0876CA91. Disassemble each of these addresses. Be sure to convert each address into an even number by subtracting 1. Here is what we have:
The second and fourth routines simply contain bx lr, meaning they do nothing at all. There's no reason to trust either of them. The first one is the joypad routine - very promising. Take the pointer to this routine (0x087384A1), byteswap it (0xA1847308) and search the ROM for it with a hex editor. There's only one result, and it is definitely inside the Phantasy Star executable. This pointer is located at 0x007383FC. Attach the C4 codetype (F8 for Gameshark) and the 000084x3 value (000001x3 for Gameshark). Back in the ARM assembly, the first bx instruction was bx r0. So, the x is replaced with 0. The final code is C47383FC 00008403 for AR and F87383FC 00000103 for GS.